The Colonial Pipeline Cyberattack Emphasizes What Americans Want — Government to Prioritize Cybersecurity
A new Tanium poll finds support for more private sector involvement. But spending must be targeted in the right areas.
President Biden signed an executive order on cybersecurity last week following a ransomware attack on Colonial Pipeline. The order aims to strengthen cybersecurity for the federal government and outlines new security standards for software used by businesses and people.
New research commissioned by Tanium and conducted by The Harris Poll finds that most Americans want the government to prioritize security. They want more federal spending, more information sharing and more involvement from private cybersecurity companies.
This insight will be useful for policymakers and private companies alike. But where should that spending be targeted? For optimized results, government security needs to focus on reducing complexity as well as cyber risk. That means consolidating onto industry-leading platforms for enhanced visibility and security.
Cyber is everywhere
Cybersecurity has gone mainstream. We found that 54% of Americans have read or heard either “a fair amount” or “a great deal” about attacks targeting government entities and private companies over the past year.
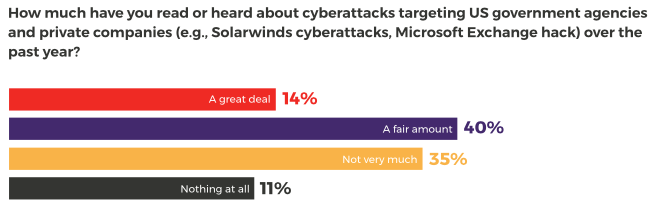
This should come as little surprise. The SolarWinds revelations highlighted the increasing sophistication of attacks targeting public and private sector organizations. Nine federal government agencies are thought to have been compromised in a months-long campaign.
Shortly after, multiple attack groups exploited known vulnerabilities in Microsoft Exchange Server in another defining moment. An estimated 30,000 endpoints in the US alone were thought to have been compromised after a widespread failure to patch promptly.
Now this month, a ransomware attack hits Colonial Pipeline, one of the nation’s largest pipelines, which has reinforced the immediate impact of cyber on Americans — they can’t fill up their gas tanks.
This kind of cyber hygiene — having 100% visibility into your IT landscape, understanding the status of your IT assets and rapidly applying updates as required — should be table stakes for any CIO or CISO.
What the public thinks about cybersecurity
Yet, the ongoing barrage of bad headlines has only added extra urgency to President Biden’s words.
There are growing concerns that the US and its allies are losing the battle against increasingly audacious hostile nations and well-resourced organized cybercrime.
We found a third (33%) of Americans believe defending against such attacks should be a top priority for the federal government this year. And while they feel the responsibility for this lies equally between government and the private sector, a plurality of nearly half (48%) think the private sector is best placed to take on the work.

How should this vital work be done? A majority (84%) of Americans believe government agencies, the military and private companies should share more information and partner to prevent cyberattacks. This would help to break down traditional silos, which slow incident response and prevent the sharing of best practices.

A similar number (80%) argue that more cybersecurity spending is essential by the federal government to improve protection. It’s important to recognize that this money must be focused inward to government agencies and used to enhance security and standards among suppliers and critical infrastructure providers.
More than half (59%) of those who want more government spending on cyber believe that this should come even at the expense of funding for other areas such as transportation, infrastructure and education.
Mitigating cyber risk with visibility and control
The message from the American people couldn’t be clearer. But effective cybersecurity doesn’t just mean more spending — it means allocating funds to the right areas.
Endpoint devices represent a critical intersection of users, data and machines, making them a prized target for attackers. Having the tools to gain visibility and control of these assets — laptops, desktops, servers, cloud containers or virtual machines — is vital to continuously mitigating cyber risk.
Yet global organizations are currently using a number of separate security and operations tools to manage their IT environments — many of which won’t work together.
This kind of “tool bloat” can harm efforts to enhance security. It compounds IT operations security silos, creates visibility gaps and means distributed teams work from different data.
The Tanium approach to endpoint management and security
Instead, agencies need to develop new strategies for managing and securing their endpoints and the data that flows through them. The goal should be to unify IT operations and security teams around a single platform, offering a comprehensive, real-time view of their entire IT environment.
The same platform must support rapid action at speed and scale, such as patching all endpoints exposed to a new zero-day threat. And it should work seamlessly with third-party offerings to provide an extended ecosystem of solutions that add additional value for the customer.
Following a strategy like this will enable government organizations and private enterprises to:
- Minimize the number of IT operations and security tools they need — reducing cost, complexity and IT risk in the process.
- Reduce the number of interfaces they use for security functions.
- Minimize the overhead and friction between teams working together to secure the organization.
- Ensure they have visibility and control of their most critical IT assets.
- Continually verify and maintain cyber hygiene throughout their IT infrastructure.
Download the full report, Harris Poll Survey: Cybersecurity Investments and Priorities.
To find out more on the changes in President Biden’s executive order on cybersecurity, visit this site Strengthening Cybersecurity Defenses.
Survey Methodology
This survey was conducted online within the United States by The Harris Poll on behalf of Tanium from April 22-26, 2021, among 2,063 adults ages 18+. This online survey is not based on a probability sample and therefore no estimate of theoretical sampling error can be calculated. For complete survey methodology, including weighting variables and subgroup sample sizes, please contact [email protected].



