Cybersecurity: Global Threats Require a Global Response
Cybersecurity: Global Threats Require a Global Response
Cyberattacks mounted by nations and nation-states against private companies — and each other — are nothing new. But their boldness, frequency, and sophistication have steadily increased.
In this blog, we’ll take a look at how a recently developed Tanium connector for OpenCTI gives organizations the kind of threat intelligence they need to more quickly identify and remediate cyber threats.
“Right now, cybersecurity is being provided by individual companies,” Jerome Warot, vice president, technical account management, Tanium, explains. “Vendors are providing solutions, but the globalization of threats means that countries have to start working together. And the best way to do that is with communities that cross borders and build open, flexible cybersecurity and threat intelligence platforms.”
Warot draws an analogy with the way the world has formed alliances to fight the COVID-19 pandemic.
“The pandemic is a global problem,” Warot continues. “And labs across the world are starting to work together to address that with vaccine and testing development and sharing research. In the case of cybersecurity, OpenCTI gives people the chance to share knowledge to combat threats.”
What is OpenCTI?
OpenCTI (Open Cyber Threat Intelligence) is an open-source platform that allows organizations to manage cyber threat intelligence knowledge. It was created to structure, store, organize, and visualize technical and nontechnical information about cyber threats.
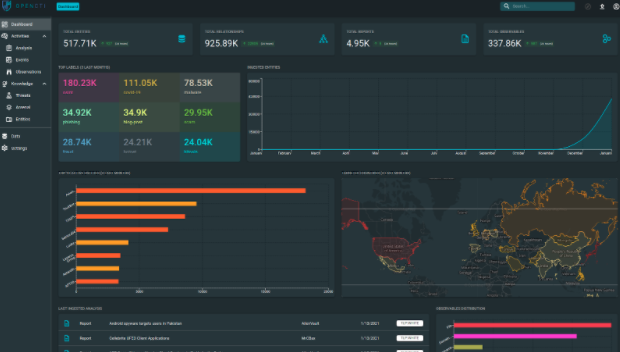
OpenCTI Landing Page Dashboard
Its development originated with the French national cybersecurity agency (ANSSI) and the CERT-EU (Computer Emergency Response Team of the European Union). Since then, the platform has been released in open source and made available to the entire cyber threat intelligence community.
Tanium and OpenCTI
Prior to joining Tanium as its director of security strategy and operations, Samuel Hassine was the head of cyber threat intelligence for ANSSI. He knows just how powerful the Tanium platform can be when connected to OpenCTI.
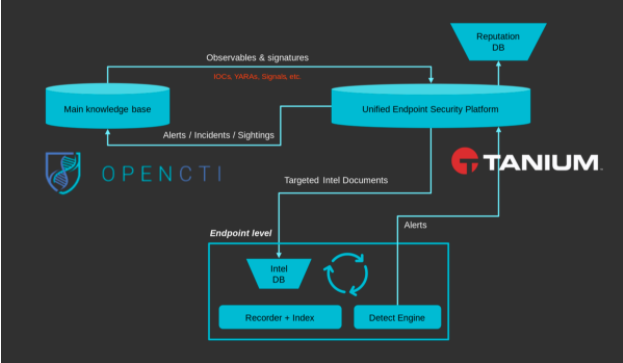
High-level design of the integration between Tanium and OpenCTI
“Tanium is like a powerful car with what it can do in terms of detection, responding to cyberattacks, and the forensic capabilities of its Threat Response module,” Hassine says. “A car needs fuel. Tanium already provides out-of-the-box behavioral signatures while the integration with OpenCTI brings other types of indicators to increase the global coverage.”
The connector takes threat intelligence data from OpenCTI and delivers it to Tanium for threat hunting and detection purposes. OpenCTI also has connectors to gather threat intelligence data from open or closed sources such as FireEye, FS-ISAC, AlienVault, Kaspersky, VirusTotal or MISP (Malware Information Sharing Platform).
“OpenCTI has connectors with many cybersecurity vendors,” Hassine explains. “This allows organizations to gather intelligence from various sources and have it in one place. Then it’s much easier to use signatures or indicators in detection or threat-hunting activities. And the connectors are all open and free to use.”
Data quality, context and speed
The OpenCTI connector allows organizations to select the threat data that’s most relevant to their industry and their security posture. They can configure data sources with different confidence levels. And when investigating an alert or threat indicator, analysts can refer to OpenCTI to see the signature of a threat and review context about it, such as its attribution to threat actors and tactics used by targets in response.
One of the biggest challenges for organizations, besides having good data, is reducing the time it takes to identify whether an event is representing a malicious activity. For an analyst, having the data and context provided by OpenCTI may significantly reduce the amount of time needed for qualification.
The cyber threat intelligence provided by OpenCTI can be used in several ways. For example, it could be used to search a data lake for potential threats. And, as mentioned, it can feed a forensics, detection and remediation tool like the Threat Response module in Tanium.
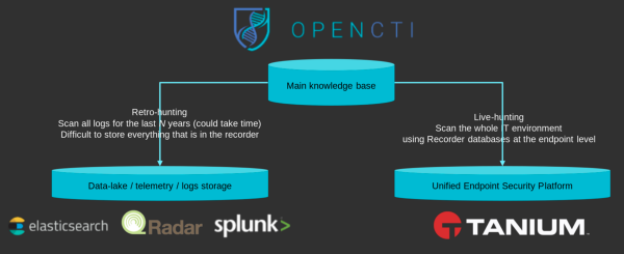
The two different threat hunting models
OpenCTI data also contains detection and remediation guidelines for different classes of threats. Of course, the data can inform executive and board-level reports on a company’s security posture and potential vulnerabilities.
But it’s important to remember that OpenCTI cannot take action on its own.
The OpenCTI platform is constantly changing
As the OpenCTI platform matures, its own data hub is growing. OpenCTI also constantly maintains its data source connectors, and follows a once-a-month release cadence for the platform. Tanium’s open architecture makes it a natural fit for an integration with OpenCTI.
“Tanium is unique because it’s quite open,” Hassine says. “Other endpoint detection systems are difficult to integrate because they have their own threat intelligence feeds. But with Tanium you can connect to other data sources to enhance your detection capabilities.”
That flexibility also means that organizations can choose the data feeds from OpenCTI that best fit their business. They don’t have to take everything available. They can take intelligence relevant to a market, vertical, or particular threat or threat vector.
Trends in threat hunting and vulnerability detection
“When I started to work on OpenCTI, it was for the internal needs at the French National Cybersecurity Agency,” Hassine recalls. “We lacked a tool like that. And we couldn’t find it commercially. So we started development and I never thought it would have such an impact or that so many people would want to use it.”
Hassine feels that this is an indicator of how the field of threat hunting and vulnerability detection is changing. It’s becoming much more data driven, even among organizations that are relatively immature in terms of cybersecurity.
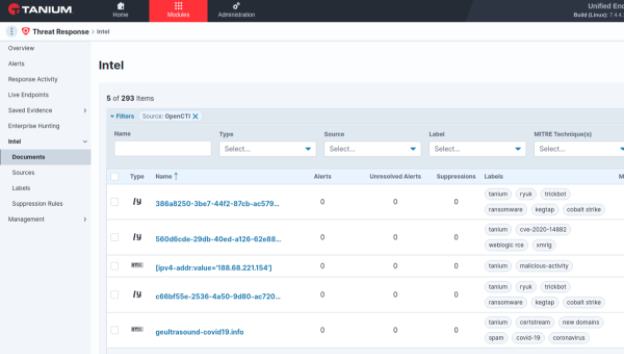
The Tanium Threat Response repository of intels
“What I’m seeing in the field is that people have started to understand what cybersecurity is and what they need to do,” Hassine says. “Organizations want to build their cybersecurity capacity, but they have limited resources. So they need to prioritize.”
Since it can take years to build a comprehensive detection capability, data can support the effort to prioritize and reduce an organization’s attack surface. Data provides a roadmap for prioritization, so organizations can address the most prominent threats.
“It’s like malicious, massive phishing,” Hassine muses. “You don’t try to spear every fish. You go after the most dangerous ones. Most of the teams in charge of developing detection capabilities understand this and they are using threat intelligence to prioritize their development and integrations. No system can address all tactics and procedures; you have to make choices.”
In their efforts, the usage of the MITRE ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) framework as a comprehensive matrix of tactics and techniques used by threat hunters, red teamers, and defenders to better classify attacks, could turn to be very helpful.
“Let’s say you estimate your coverage is almost 60 percent of the framework,” Hassine says. “You will quickly figure it could take years to address the remaining gaps. Using relevant Cyber Threat Intelligence data can definitely help to prioritize the next moves.”
The Tanium-OpenCTI connector is now ready for production use and available to all Tanium customers.
“The connector takes advantage of the latest technical advances in the OpenCTI platform, which provides a real-time events stream of threat intelligence data. Tanium Platform is therefore fed in real time with the latest signatures and indicators,” Hassine says. “It’s not difficult to install. Configuration is easy. What’s tricky is knowing just what kind of knowledge you need. You can’t bring everything into Tanium. You have to choose and that requires some cybersecurity expertise.”
Read more about the announcement of the OpenCTI connector in the press release.
To get more detailed information and documentation for setting up the connector, visit this website.




