5 Ways Tanium Impact Helps Businesses Guard Against Lateral Movements in Cyberattacks
The most effective way to reduce an attacker’s ability to engage in lateral movement is by having clear, detailed and actionable reporting about users, endpoints and groups
Lateral movement means using stolen credentials to move from computer to computer in a cyberattack.
Nearly all cyberattacks involve lateral movement. Attackers sneak into one computer, access the login credentials active on that computer, and then use those credentials to move to other computers, such as laptops, desktops or servers.
Lateral movement lets attackers fulfill their mission: installing ransomware on as many computers as possible or searching for any valuable data on the corporate network, such as credit card data stored on servers.
In some attacks, lateral movement is a slow, cautious and stealthy process managed by a remote human attacker. In other attacks, it’s a lightning-fast traversal of endpoints automated by malware that takes advantage of lax administrative permissions or unpatched vulnerabilities.
When the NotPetya worm struck the computer network of Moller-Maersk, the world’s largest shipping container company, in 2017, the malware spread across the international company’s global computer network within minutes, shutting down operations and eventually costing the company $300 million.
One way that IT organizations can guard against lateral movement is by limiting user permissions. Ideally, each user’s access privileges should be limited to the privileges they need for performing their job. Users should not have access to accounts or endpoints without having an explicit reason.
Unfortunately, keeping track of user permissions can be difficult, especially in organizations with thousands of users and endpoints along with tens or even hundreds of user groups. In most organizations, determining who has access to what is time-consuming and error-prone work. And too often, it’s an afterthought.
Tanium Impact helps security teams discover and reduce lateral movement paths
To provide IT organizations with the visibility they need to analyze access rights and the vulnerabilities they pose, Tanium created a new module called Impact, a software offering included in the Tanium Platform for managing endpoints with unparalleled visibility and control.
Tanium Impact analyzes relationships between users, groups, and endpoints at speed and scale to identify lateral movement potential. It provides the ability to visualize and contextualize the administrative realm and lateral movement risk, empowering prioritization of remediation efforts.
Here are five ways that Tanium Impact helps IT organizations guard against lateral movements in cyberattacks.
1. Tanium Impact shows possible lateral movement paths to and from the users, groups, and endpoints analyzed.
Impact provides an easily understood graphical representation of lateral movement potential. Instead of requiring security analysts and operations engineers to zoom in and pan across complicated network diagrams, Impact presents a clear series of links to and from each user, group and endpoint.
For a comprehensive analysis of lateral movement, Impact reports on both inbound and outbound paths. Inbound paths show which other accounts and endpoints can log into an endpoint from another endpoint on the network.
Outbound paths show which other accounts and endpoints an endpoint itself can access — and hence which other endpoints might be vulnerable if that endpoint is compromised.
Both views are essential for understanding the security risks about a particular user account or endpoint.
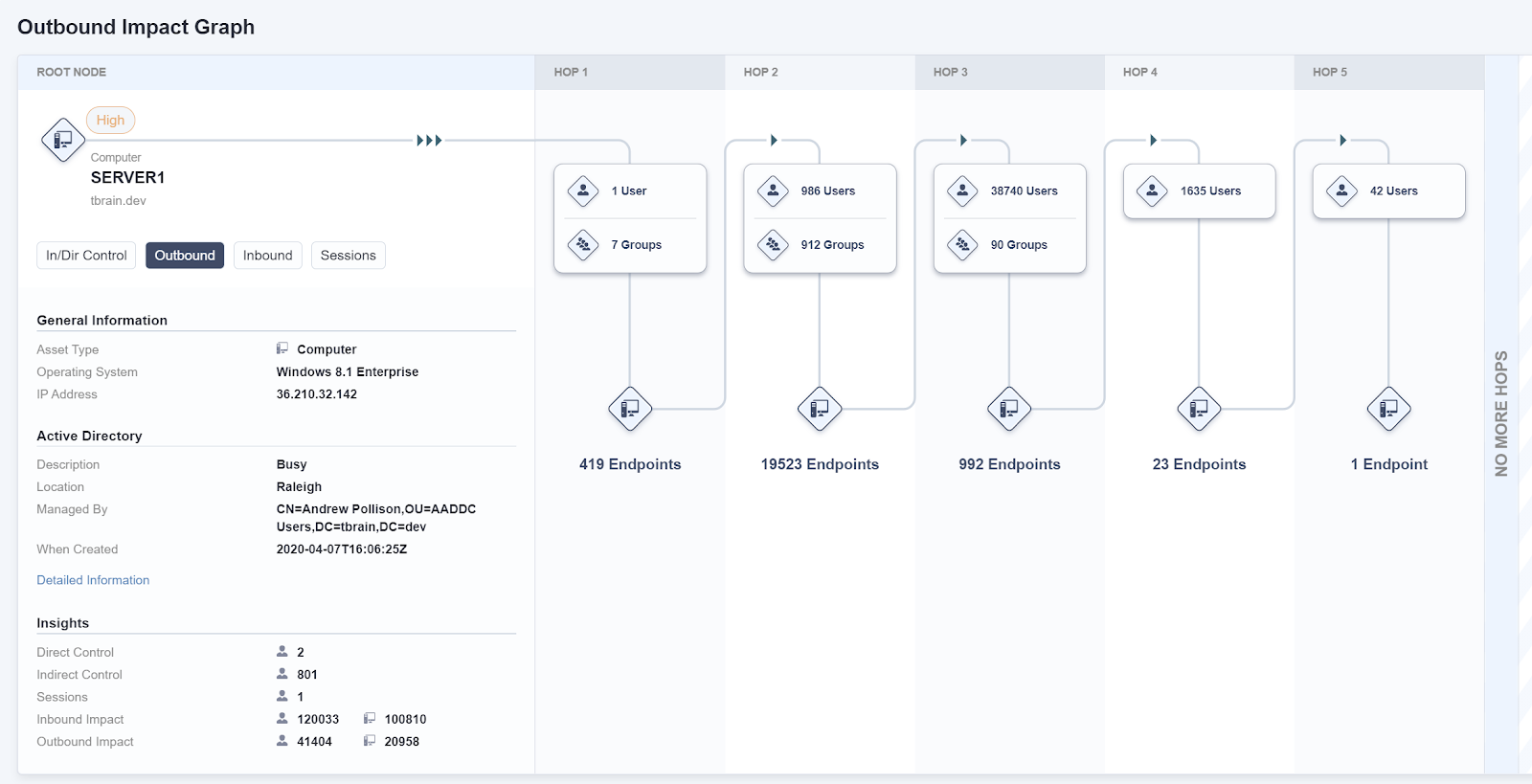
The Outbound Impact view shows lateral movement potential FROM the endpoint of interest.
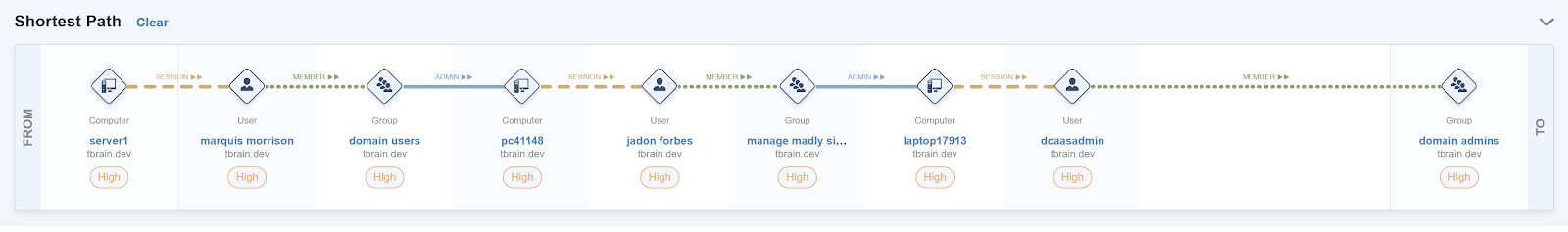
Clicking the target icon next to an asset in any of the tables brings up a shortest path graph.
2. Tanium Impact reports access data for an entire enterprise, not just a local network.
In large enterprises, security teams must understand the risk of lateral movement across its endpoints, not just those in a particular location. After all, with access to login credentials, attackers can quickly move from one office network to another.
Impact displays access paths across the entire enterprise. It’s a single, comprehensive reporting tool that scales to cover thousands — even hundreds of thousands — of endpoints distributed across multiple offices, regions, and data centers.
No matter how large the network, IT teams can use Impact to understand and manage risks associated with lateral movement for their endpoints under management.
3. Tanium Impact includes session data in its analysis of lateral movement, helping analysts understand the risks associated with attacks that began hours or even days ago.
When a user logs into an account on an endpoint, that login credential may remain in the endpoint’s memory until the endpoint is rebooted. Attackers use credential theft tools like Mimikatz to read login credentials, hashes, tokens, and PINs out of memory, so they can be used for accessing other endpoints.
By keeping track of which credentials have been exposed to endpoints, Impact helps security analysts understand the security risks associated with the user or endpoint.
Collecting this information is important for stopping lateral movement in action. When security analysts detect a network intrusion, they need to work as quickly as possible to discover which endpoints have been compromised and which user permissions on that endpoint might be used to compromise other endpoints.
Tanium Impact collects this information going back 72 hours, helping analysts trace lateral movements quickly, even for attacks detected a day or two after they began.
4. Tanium Impact analyzes both direct control and indirect control when evaluating the potential movement of an endpoint, user or group.
Direct control means a user has administrative control over an endpoint.
Indirect control means a user belongs to one or more groups with administrative control over an endpoint.
To understand the risk of lateral movement, security analysts need insight into direct and indirect control for their endpoints.
In many organizations, access permissions become more complicated over time. Users are assigned to groups, and some of those groups are later assigned to other groups, which may, in turn, be assigned to yet other groups.
Nested group structures can be complicated, but security analysts need to understand them if they are going to be able to effectively manage the risks associated with any particular user, endpoint or group.
By analyzing both the direct and indirect control users have over endpoints, along with session data, Impact gives security teams the comprehensive visibility they need for assessing the risk of lateral movement and reducing that risk as much as possible.
The Indirect/Direct Control view shows the administrative realm for the endpoint of interest.
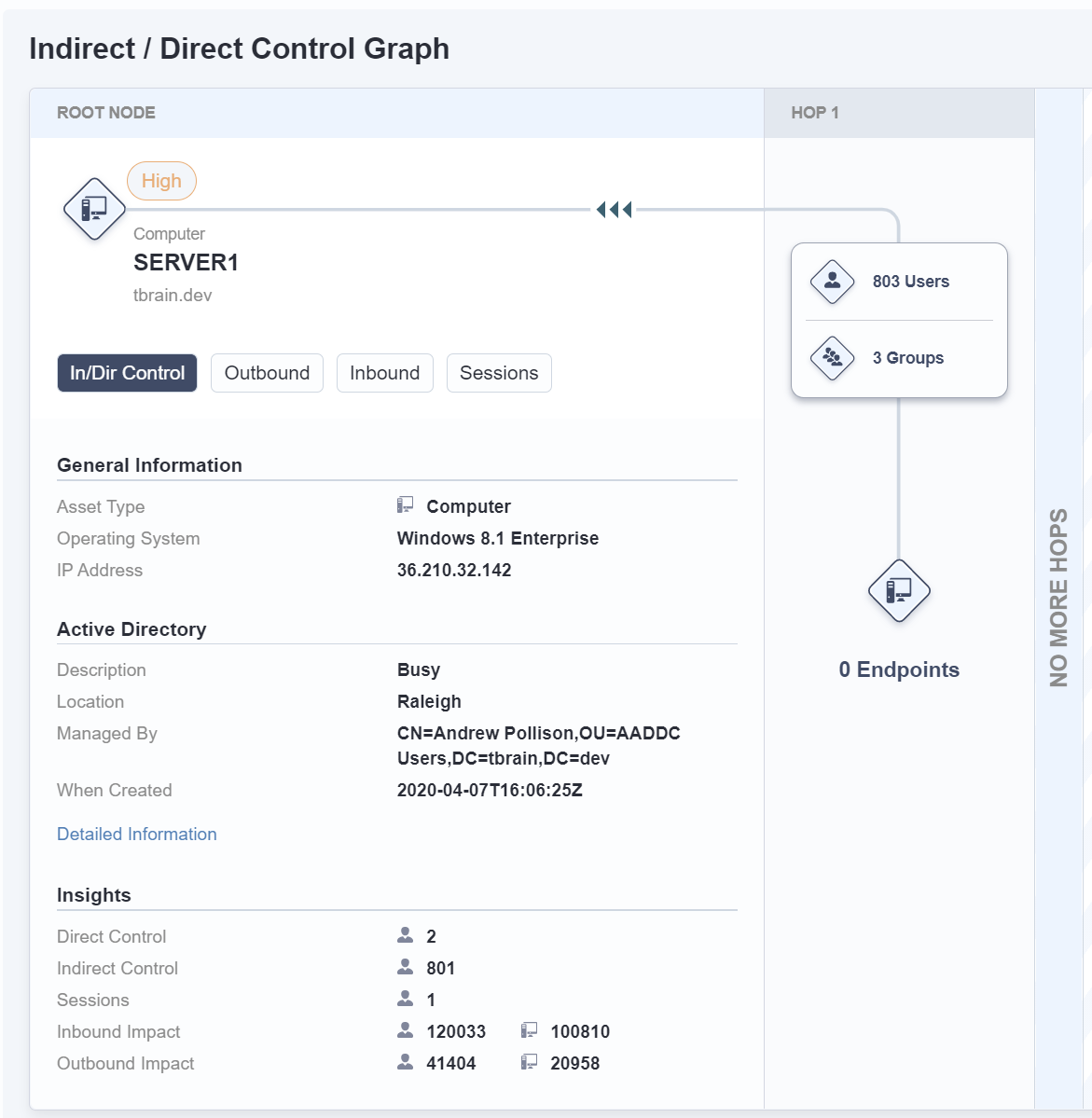
The Indirect/Direct Control view shows the administrative realm for the endpoint of interest.
5. Tanium Impact assigns an impact Rating to users/groups/endpoints, so IT organizations can easily prioritize the endpoints and user accounts that require attention for risk mitigation.
Tanium Impact analyzes permissions and assigns impact ratings to endpoints, users and groups based on the exposure they create for attacks using lateral movement.
Four factors influence an impact rating:
- Potential inbound impact by users
- Potential inbound impact by endpoints
- Potential outbound impact by users
- Potential outbound impact by endpoints
Assigning an impact Rating to users/groups/endpoints helps security teams in two ways.
- First, it helps them prioritize proactive remediation of lateral movement risk.
- Second, it helps security analysts prioritize alerts they receive from Tanium Threat Response or other security reporting tools. Suppose a security analyst sees two alerts, and one has a low score for a chance of lateral movement, and another has a critically high score. In that case, the analyst knows to investigate the device’s alert with the high score first.
Tanium Impact provides visibility essential for effective cyber defense
As recent cyberattacks have shown, criminals can move quickly across almost any enterprise network they infiltrate. Through lateral movement, attackers can broaden the scope of their attacks and increase the odds of discovering a business’s valuable digital assets.
To reduce an attacker’s ability to engage in this movement, IT organizations need clear, detailed and actionable reporting about users, endpoints and groups.
Tanium Impact, available at no extra cost as part of the Tanium Platform, provides the insights that IT organizations need for countering lateral movement.
Tanium Impact provides clear visualizations and risk analysis that help IT organizations act effectively, whether proactively engaging in risk management or quickly responding to threats.
Learn more about Tanium Impact during this webinar, Gaining Visibility of Lateral Movement.
Ready to see it in action? Request a demo today.




