IT Hygiene Begins With Asset Discovery and Inventory
All companies, regardless of size, need asset inventory information, which in modern IT changes constantly as assets come and go
For people, hygiene is a series of practices performed to preserve health and prevent the spread of disease. But we’ve humanized computers to the point where we apply the concept of hygiene to IT.
Basic IT hygiene should ensure that all systems run well, are properly managed and secured against threats.
To preserve and improve IT hygiene, you first need to know what IT assets you have. Do you have 50,000, 100,000 or 500,000 computers and servers in your organization? Where are they? What are they? What’s running on them? What services do they provide?
Answering those questions is what asset discovery and inventory is all about. It’s the foundation for IT hygiene. In this blog, I’ll dig into why that foundation is so important.
You can’t manage what you don’t know you have
To manage your endpoints, you need three levels of knowledge:
- What assets do you have, and where are they?
- What software is running on them, and are they licensed? You need more than a hostname or an IP address.
- How do the machines on your network relate to one another, and what is their purpose? In the world of servers, for example, you may have a group of servers that exist solely to host a service, like a company website.
All companies, regardless of size, need this information, which in modern IT changes constantly. Network assets come and go, especially with “bring your own device” (BYOD), a common and growing policy in many organizations. Some assets may appear on the network only occasionally. With more companies encouraging employees to work from home (WFH), complexity increases.
Know what you have at all times
The operational disadvantages of not knowing
To paraphrase former Eagle Don Henley, when you drive with your eyes closed, you’re bound to hit something. When you don’t know what assets are on your network, it’s the IT equivalent of driving with your eyes closed.
One of the first things you’re likely to “hit” is security vulnerabilities. If you can’t manage an asset, you can’t secure it. And you can’t manage it if you don’t know you have it. You won’t know whether software is patched properly. So there may be attack vectors you’re entirely unaware of.
How about financial implications? Do you have a general sense of what you’re spending money on? Take software licensing, say a popular productivity program like Microsoft Office. If you have a license for 10,000 copies, do you use 20,000 or only 5,000? Do you efficiently use the license you pay for? Or are you out of compliance where you may be subject to expensive legal action?
Moreover, compliance isn’t just about software licensing. And it’s another area of operations that’s very dependent on knowing what assets are on your network.
Let’s take healthcare as a use case. Healthcare companies must prove compliance with HIPAA and PCI provisions that cover protected health information and credit card data. Do you know where that data lives? If not, you can’t prove compliance. Inability to prove compliance has two significant downsides: regulatory sanctions and unhappy customers.
What features are important for a toolset intended for asset discovery and inventory?
The tools or platform you use for asset discovery and inventory should possess:
- Accuracy
- Speed
- Scale
- Ease of use
Accuracy, speed and scale are closely related. If it takes two weeks or a month to do an inventory, by the time you’re finished, the network has changed, and you’ve undoubtedly missed something.
It’s no longer accurate, no matter how diligent you were. The bigger the network, the more of a problem this presents. That’s why scale matters. Ease of use comes into play because a tool that’s hard to configure produces errors, and over time, people won’t want to use it.
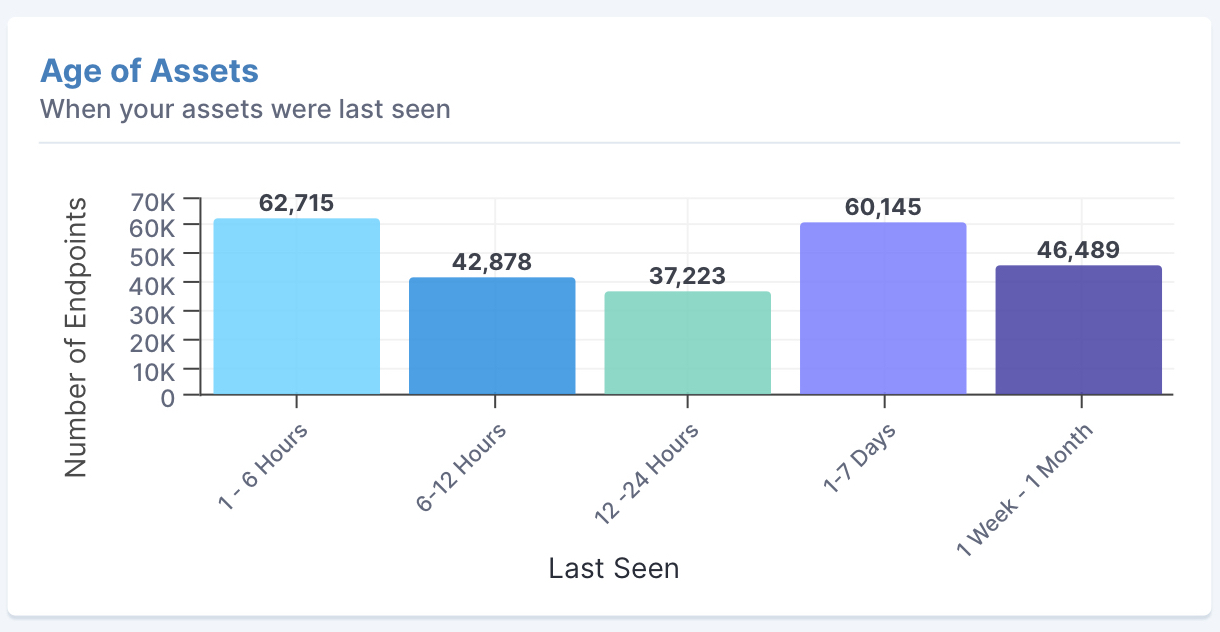
Know the age of each asset
Older tools have a hard time with the demands of modern IT
Asset discovery tools built 10 years ago preceded many of the things modern IT environments operate with daily. Two examples: containers and hybrid clouds.
These tools can’t handle the rate of change we see now. Yet organizations often remain attached to the tools they’re comfortable with, many of which are not easy to use. In fact, they may take pride in mastering hard-to-use tools. Maybe they wrote custom scripts to make them work more effectively. Not only that, an entire partner ecosystem has grown up around helping IT departments do just that.
The unintended — and unfortunate — consequences of that are IT policies and processes crafted not because they’re the best way to address an issue but because they fit the capabilities of the tools in use. It’s the IT version of “if you have a hammer, everything must be a nail.” The policies are: “We must nail things.” Entrenched tools become part of the IT ecosystem. But the best IT policies should be tool-agnostic. A tool built in 1993 — or 2010 — can’t offer that flexibility.
Endpoint discovery is a constantly moving target
Not every endpoint on a network is a desktop computer, laptop or server. There are printers, phones, tablets and a growing number of consumer and industrial internet of things (IoT) devices. Mobile device management (MDM) is a growing application field. With an MDM provider like Microsoft Intune, you can track all the phones on your network.
But why should you have to worry about a consumer IoT device compromising the corporate network? Here’s why: An employee of one of our customers was working from home. The company’s security team was receiving alerts that someone was trying to break into her laptop. The source was a refrigerator with malware scanning her home network and trying to get into her device, which was temporarily on the corporate network. The same thing could occur with a smart light switch, thermostat, security camera — you name it.
This is also true of machines on the factory floor, many of which are equipped with sensors that communicate via wireless networks and the web with manufacturing applications. It’s a field called operational technology, and, in essence, it makes every machine on a factory floor a network device.
No single asset discovery tool can discover every device type, so the tool or platform you use must integrate with applications that can recognize devices like phones, tablets, printers, etc. That requires a toolset that can work well with supporting applications. It’s why, for example, Tanium is building an integration between Tanium Discover and Microsoft Intune for mobile device inventory.
Endpoint discovery is the foundation of Zero Trust solutions
When everything is a network device, everything is a potential security vulnerability. So you need policies and procedures that break endpoints into three categories: managed, unmanaged and unmanageable. Endpoint discovery is the first crucial step in the trend toward Zero Trust solutions. CSO online describes Zero Trust as “a security concept centered on the belief that organizations should not automatically trust anything inside or outside its perimeters and instead must verify anything and everything trying to connect to its systems before granting access.”
Threat response and remediation tools are only as good as the breadth of endpoints they’re running on. So endpoint discovery really is where IT hygiene and security begin. You have to start there.
To learn more about the role of endpoint discovery in Zero Trust implementations, check out our blog post, Endpoint Identity: The New Center of Gravity in a Zero Trust World.
For more information on the Tanium Asset Discovery and Inventory solution, read our blog post 9 Ways Tanium Makes Asset Discovery and Inventory Faster, Simpler, Easier and — Better.
If you’re ready to see it in action, sign up for a demo today.




