Shutting the Door on the Microsoft Exchange Server Attacks With Tanium
With cybersecurity attacks increasing, businesses need to be ready for whatever comes next. Learn how proactive prevention and rapid response with Tanium helps mitigate risk.
At Tanium, we’ve been talking for years about the need for enterprises to gain comprehensive visibility and control of their IT assets. But how bad could things really get if you neglect these best-practice principles? Look no further than the rapidly escalating attacks targeting Microsoft Exchange Servers around the world.
It goes without saying that a security breach of this criticality could lead to significant financial and reputational damage, either via lost intellectual property (IP) and regulated customer data or extended ransomware-related outages.
No doubt there will be more weeks like this in the years ahead. And you need to be ready for whatever comes next. That means real-time visibility, comprehensive control and rapid response with Tanium.
What happened with the Microsoft Exchange Server attacks?
First spotted back in early January, the attacks exploited four zero-day bugs in on-premises versions of Microsoft Exchange Server, for which Microsoft issued emergency out-of-band patches last week. It said:
“In the attacks observed, the threat actor used these vulnerabilities to access on-premises Exchange servers which enabled access to email accounts, and allowed installation of additional malware to facilitate long-term access to victim environments.”
Early reports suggested as many as 30,000 servers in the US had been compromised and possibly more than 100,000 globally. One noted journalist and researcher described any unpatched Exchange Servers as a “ticking time bomb.” This judgment appears to have been borne out by news that multiple advanced persistent threat (APT) groups quickly rushed in to exploit the same zero-day bugs.
What does it mean for my organization?
Typically, the attackers deployed web shells to achieve persistent remote access to victim servers. They stole credentials from the compromised servers to move laterally inside targeted networks. This could theoretically enable them to find and steal sensitive data, deploy ransomware, and possibly even scope out other vulnerable endpoints that could be exploited later.
The White House and the US Cybersecurity and Infrastructure Security Agency (CISA) have both expressed concern about the attacks and their consequences. CISA told government agencies to patch immediately or else disconnect their on-premises Exchange Servers.
Time for Tanium
If you think of endpoints like Exchange Server as the doors and windows of your house, Tanium helps you lock and bolt them so that no one can enter in the first place. This is always the optimum course of action, as proactive prevention is cheaper in the long run and more effective than reactive approaches.
But if the worst-case scenario does happen, Tanium also provides a powerful flashlight for you to check inside for intruders.
In summary, Tanium offers:
Proactive protection via Tanium Patch and Tanium Interact to achieve best-practice cyber hygiene.
Tanium Patch can be used to patch vulnerabilities at speed and scale using normal workflows. It can be deployed to automate patching of critical endpoint assets so that the chances of exposure are reduced like the recent ones impacting Exchange Server.
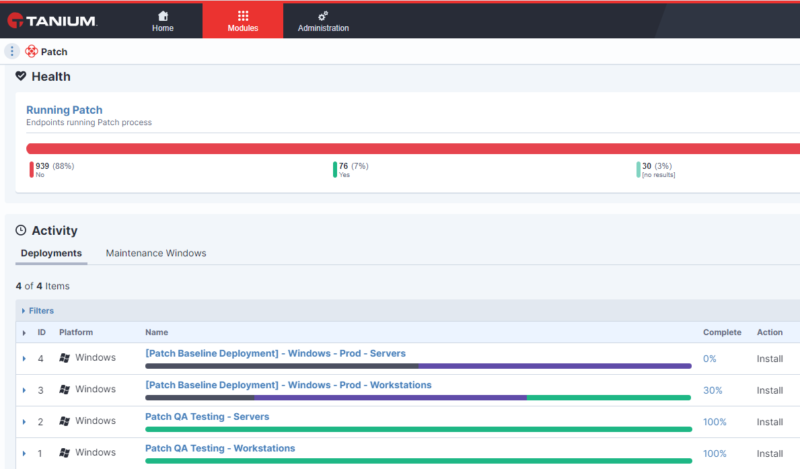
With Tanium Patch, you can understand patch status immediately.
Tanium Interact allows you to quickly and easily query whether you have vulnerable endpoints (such as Exchange Server) and get answers back in real time, across thousands or even hundreds of thousands of IT assets. This article shows how customers could have done so as soon as Microsoft released the out-of-band patches.
Tanium Impact also helps organizations take a more proactive stance on cyber risk management by mapping out where attackers may move next if they compromise a particular endpoint. This allows you to plan for and disrupt any potential malicious actions.
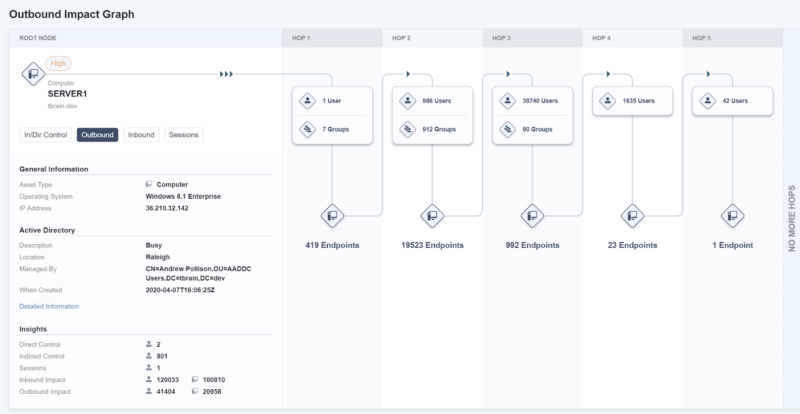
The Outbound Impact view shows lateral movement potential from the endpoint of interest.
Detection and response via Tanium Impact and Tanium Threat Response. If an adversary has managed to compromise an endpoint, these tools work in concert to help you react with speed and precision. Threat Response continuously monitors for multiple credential theft and lateral movement techniques, while Impact can tell you where the bad guys may be going — helping you track them down and kick them out.
Patching isn’t enough. Investigate each affected endpoint, and activate your Incident Response plan if signs of compromise (such as webshells) are found.
Ready for anything
These attacks were not the first of their kind, and they won’t be the last. The speed at which these vulnerabilities were exploited should drive home the need for proactive prevention through good cyber hygiene and rapid response to mitigate threats before they’ve had a chance to impact the organization.
In fact, recent research revealed that 63 percent of vulnerabilities recorded last year were low complexity and 68 percent required no user interaction to exploit. Both portend a challenging future for organizations stuck in reactive firefighting mode.
IT leaders have been stretched to the limit over the past year, supporting the mass shift to distributed working and new business priorities.
According to a Tanium study, most (93 percent) delayed critical security priorities as a result. We may be seeing the impact of those decisions today.
Going forward, we can’t keep making the same mistakes. Your organization needs to be ready for whatever comes next — with real-time visibility, comprehensive control and rapid response.
For more detailed information on how customers can address this vulnerability with Tanium, check out this article on our Tanium Community.
To learn more about how the Tanium platform can help find and remediate vulnerabilities, visit our website. You can also sign up for a free trial to see it in action in your environment.