10 Ways Tanium Improves Data Risk and Privacy
How do you manage data risk across increasingly complex IT systems?
Global organizations spent hundreds of million on compliance with data protection regulations in 2019. That’s a powerful indicator of just how far up the corporate priority list managing data risk and privacy has risen.
It’s not just a fear of fines driving this new focus. A 2019 study found that 69 percent of consumers would actively avoid a company that has suffered a data breach.
Organizations are therefore looking for ways to effectively manage the risk of data breaches and compliance fines. But they must do so as that data moves across increasingly complex IT systems, regulations evolve, and security risks escalate. Unfortunately, many of today’s tools are ill-equipped to deal with these challenges.
Visibility is key
To achieve compliance and manage and categorize data in a responsible manner, organizations need to answer some basic questions. As a starting point, they must understand what kind of data they hold, where it is at all times, and how or if it’s secured. This has become an increasingly challenging task. Many new data privacy regulations, like GDPR in Europe and CCPA in California, not only require that data is effectively protected but also that organizations can delete it on request from their customers.
Unfortunately, these same organizations are struggling to meet their data risk and privacy obligations due to a lack of visibility into endpoint assets, which can lead to noncompliance fines.
But legacy tools are poorly architected to meet these new demands, and may even introduce extra risk by copying sensitive information to centralized databases.
Fortunately, Tanium offers a better approach to managing data risk and privacy. Here’s how.
1. Index all your sensitive data
Endpoint visibility is the foundation on which all effective data risk and privacy strategies must be built. Visibility gaps can increase cyber risk by creating significant IT blind spots of unmanaged sensitive data.
Upon installation, Tanium Platform modules perform a lightweight, distributed scan of all endpoints, applications, and files in the enterprise. From this, customers can create a comprehensive index of all their sensitive data and where it is located. Tanium typically finds up to 20 percent more endpoints than businesses thought they had, as well as finding many applications that were unaccounted for.
2. Achieve real-time awareness
Stale data is another cause of enterprise cyber risk. Without up-to-date visibility into their endpoint environment, organizations can’t react quickly to potential incidents, boost resilience through prompt patching, or provide accurate information to auditors and regulators.
Tanium allows users to ask questions of their sensitive data or endpoints whenever they want, to get real-time insight into compliance status and cyber risk.
3. Quickly search for noncompliant data
Many legacy data risk and privacy tools require a new scan every time the user asks a new question. With each scan demanding major processing power, this can have a significant impact on overall network and endpoint performance, and leads to answers that are potentially weeks old.
Tanium continually monitors your endpoint environment for changes to ensure it can answer any recurring or ad hoc questions accurately, in real time and at scale — without performing a traditional scan.
Thanks to Tanium Quick Search, users can input arbitrary text — such as a name, endpoint, or data pattern — and find instances of that text everywhere in their environment. Customers can create specific sensitive data patterns to search for, as well as custom rulesets to help narrow their searches.
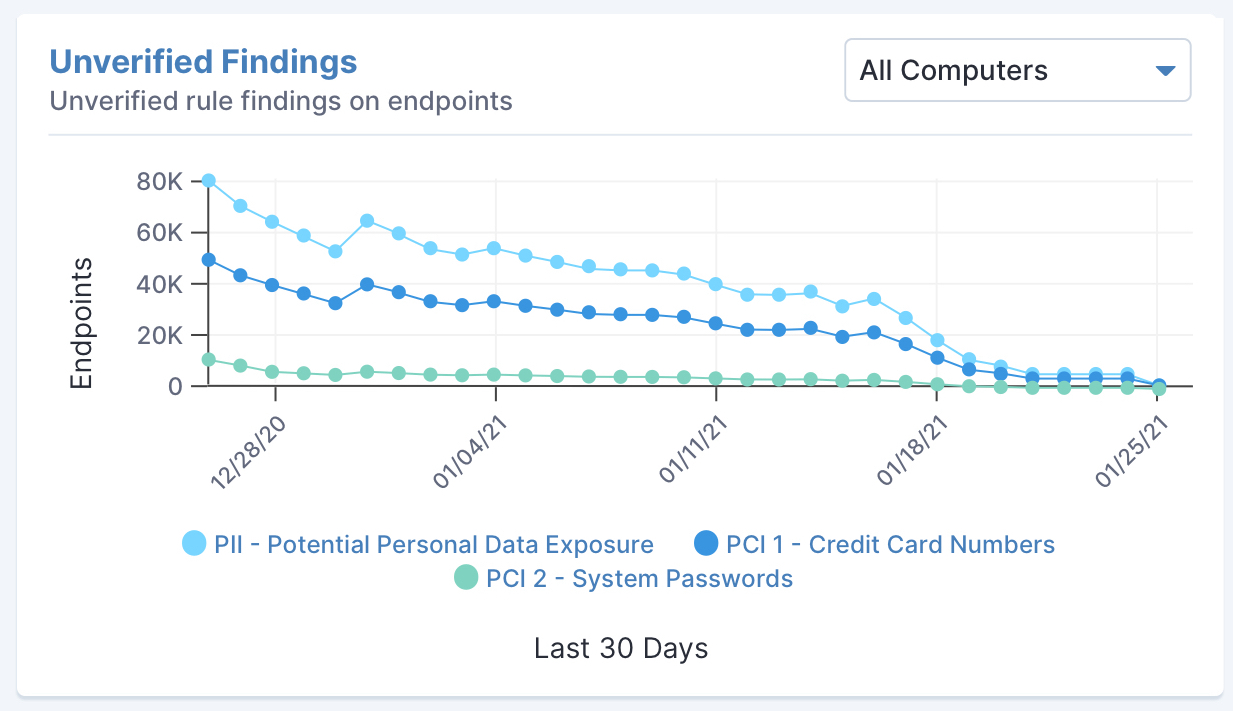
Tanium tracks unverified findings on endpoints
4. Rapidly remediate remote endpoints
Finding noncompliant data and endpoints is only half the battle. Organizations must also act quickly to remediate any issues.
That’s why Tanium features a wide range of remediation actions to help IT users resolve any detected problems with just a few clicks. This not only supports efforts to continually reduce cyber risk and maintain compliance but also helps to free staff to focus on higher-value tasks.
5. Consolidate your endpoint management tools
Over recent years, organizations have adopted an ever-growing number of point solutions to help them improve endpoint visibility and manage cyber risk. In fact, businesses use an several disparate IT security and operations tools today — adding cost, complexity, and visibility gaps.
Tanium helps to eliminate multiple point solutions by offering comprehensive data risk and privacy capabilities from a single, lightweight agent operating from a single, distributed instance.
6. Reduce data and compliance risks
Legacy solutions often add unnecessary extra risk by creating new instances of existing data and sending them to centralized databases, which may conflict with regulatory rules.
But Tanium processes all queries on the individual endpoint itself. The single Tanium instance coordinates responses to these questions, but no sensitive files are copied back to this centralized location — eliminating the risks associated with data duplication and transit.
7. Connect and expand your data protection ecosystem
Although Tanium consolidates a wealth of data risk and privacy functionality onto a single platform running on a solitary agent, we also support open integrations to help customers drive value from their broader investments in other data risk and privacy tools.
Tanium integrates with existing data governance frameworks such as GDPR, CCPA, HIPAA, and PCI DSS to streamline compliance. And it’s why we offer open APIs with many third-party vendors and orchestration platforms.
8. Automate key tasks and processes
IT and compliance teams are working flat out to support the increasingly complex and resource-intensive demands placed on them. That’s why Tanium has tried to make life as easy as possible for users by building in as much automation as possible.
With Tanium, endpoint queries and distribution of their findings can be automated over time to streamline the process of uncovering and remediating instances of noncompliance. Users can also discover and integrate sensitive data patterns into alerts and workflows, and automate validation of noncompliance findings.
The cumulative effect is to free in-house teams from repetitive tasks so they can be of more strategic use to their employer.
9. Maintain a single source of truth
Tanium’s patented architecture accelerates the data-gathering process from weeks to seconds, and delivers it as a single source of the truth. That means remediation teams and auditors have the same granular set of data to work from.
What’s more, this data is continuously updated so that IT users can access accurate answers in real time. Tanium’s high-performance, distributed architecture also means organizations can eliminate the need for the hundreds or thousands of servers they previously used to manage and protect endpoints.
10. Pick your approach: out-of-the-box to customized
Tanium delivers data risk and privacy for the world’s most demanding organizations. But every enterprise is different.
That’s why — although Tanium offers a range of out-of-the-box solutions, modules, and workflows — more customized options are also available. For customers with unique and particularly complex challenges that no prepackaged solution can solve, Tanium offers a range of enterprise services.
Getting your data risk and privacy house in order
Multimillion-dollar noncompliance fines are enough to focus the minds of any boardroom. Yet data breach and privacy incidents can also mean lost customers, legal costs, IT and remediation charges, and a hefty reputational hit.
But with the right tools to drive insight and control where you need it most, at the endpoint, you can protect your brand reputation and the business bottom line.
To find out more about Tanium Data Risk and Privacy, please contact us or check out a demo of the Tanium Platform.
You can also read my other blog post 7 Ways to Minimize Data Risk and Enhance Privacy Compliance.




