What Is Device Vulnerability Management?
Device vulnerability management uses specialized tools to monitor an organization’s devices and detect and resolve configuration issues that could open it to cyberattack.
“Device vulnerability management” refers to the process of identifying, prioritizing, resolving, and reporting vulnerabilities within an organization’s network devices and software. Bad actors can take advantage of vulnerabilities to gain unauthorized access to data and other organizational resources and potentially inflict astronomical damage.
According to the Ponemon Institute’s “Cost of a Data Breach Report 2021,” the average cost of a data breach in the U.S. is $9.05 million. The number is so high because by the time a targeted company realizes it has a breach, significant damage has already been done. The same report found it takes 287 days, on average, for an organization to identify and contain a breach.
Device vulnerability management offers a way to find and close security gaps before they’re exploited. In practice, it uses specialized tools to automatically monitor an organization’s devices and
detect and resolve system configuration issues that could open it
to cyberattack.
But it goes beyond just reconfiguring settings and patch management. At its heart, device vulnerability management is a proactive organizational mindset that understands that new vulnerabilities are identified daily and that discovery and remediation must be a continuous process.
The growing threat of cybersecurity attacks and the increasing number of regulations, such as the Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI DSS), and the General Data Protection Regulation (GDPR), have made device vulnerability management critical for every organization.
While some regulations specify quarterly vulnerability scans, these are no longer sufficient in today’s aggressive threat landscape. Reducing your attack surface and mitigating threats require an ongoing approach that provides real-time visibility into device vulnerabilities and facilitates rapid remediation.
- What are device vulnerabilities?
- What are the three steps of the vulnerability management process?
- What are the pros and cons of network-based scanning vs. agent-based scanning?
- What is a vulnerability and compliance assessment?
- How are device vulnerability reports used?
- How is device risk calculated?
- What is vulnerability remediation?
- What does a vulnerability report look like?
- What are the challenges involved with device vulnerability management?
- What should I look for in a device vulnerability management tool?
What are device vulnerabilities?
A device vulnerability is an error or misconfiguration in a device’s code base that can potentially be exploited to compromise the data within it or the network it is connected to. Threat actors can leverage device vulnerabilities to gain escalated user privileges, launch denial of service (DoS) or ransomware attacks, and otherwise cause damage. Even if they aren’t actively targeted, device vulnerabilities can often result in accidental data exposure and leaks.
Most organizations aren’t aware of a device vulnerability until a threat is present. At that point, they can only react to manage its spread and limit its damage. The nonprofit MITRE Corporation created the Common Vulnerability and Exposures (CVE) Program to help organizations proactively “identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.”Even if they aren’t actively targeted, device vulnerabilities can often result in accidental data exposure and leaks.
The CVE Program includes hundreds of thousands of vulnerability records. MITRE catalogs known vulnerabilities and assigns each one an ID. The ID includes the year the vulnerability was identified, followed by a reference number—CVE-2022-23728, for example. Occasionally, a security vulnerability will also be given a name by its creator or by the media that will become interchangeable with its CVE. BlueKeep, for example, is the same vulnerability as CVE-2019-0708. Some named vulnerabilities may also be associated with more than one CVE.
Each CVE record includes a description of the vulnerability, a link to its detailed entry in the National Vulnerability Database (NVD), and reference links to additional information. Risk severity is calculated for each vulnerability using the Common Vulnerability Scoring System (CVSS). This score can range from 0 (not severe) to 10 (critical). CVE records get updated over time as more is learned about a vulnerability or when a new exploit for it has been discovered. New information can increase or decrease its severity score.
[Read also: What is a cyber risk score and why does it matter?]
Device vulnerability management involves scanning your organization’s environment to determine if any of these CVEs are present. If a CVE was created for a vulnerability in Adobe 7.3.12, for example, it could be fed into a device vulnerability scanning tool to search the organization’s endpoints for that version of Adobe, as well as earlier versions, and identify and remediate each instance.
What are the three steps of the vulnerability management process?
Vulnerability management follows three steps:
- Identification. Identify all the vulnerabilities that exist across your endpoints using an automated vulnerability testing tool called a vulnerability scanner, which looks for misconfigurations and coding errors that pose a security risk. This scanner uses a protocol like Open Vulnerability and Assessment Language (OVAL) to encode device configuration information and other system details, and compares them against a database of known vulnerabilities, such as the CVE Program. The scanner logs any vulnerabilities it detects so they can be evaluated and prioritized. It is crucial to scan broadly and frequently to have results that are hours or days (at most) old, not weeks.
- Evaluation. Once you’ve identified the vulnerabilities on your devices, you must evaluate the risk they pose to your organization. A vulnerability’s severity score is an important part of determining the threat it poses, but you must also consider other real-world factors, such as how easily that vulnerability could be exploited or whether an exploit already exists, the potential business impact and cost if the vulnerability were exploited, and whether you have security protocols in place that could mitigate the likelihood or effects of an exploit. Other factors to weigh include where a vulnerability is found. A misconfiguration on the CEO’s laptop would probably be more critical than the same vulnerability on a temporary worker’s laptop. Taken together, these considerations should help assign a risk score for each vulnerability.
- Remediation. After you’ve identified and evaluated the vulnerabilities on your device, the next step is to decide how to prioritize and address them. The risk score you assigned to each vulnerability should help you segment them by criticality, and vulnerability scanners will often recommend how to resolve them, though this should always be balanced with input from security and IT teams. In general, there are three strategies for addressing vulnerabilities. Remediation involves patching or correcting code that contains a vulnerability to prevent an exploit. Mitigation takes measures to prevent the likelihood or impact of a vulnerability, usually temporarily until it can be remediated. You can also choose to take no action if the cost of remediating the vulnerability is greater than the impact
of exploitation.
Once these steps are completed, it’s important to repeat them to ensure that new vulnerabilities haven’t been introduced. In this way, vulnerability management is a continuous process.
What are the pros and cons of network-based scanning vs. agent-based scanning?
While both network-based and agent-based scanning are effective at identifying device vulnerabilities, there are differences between the two that may help determine which one is best for your organization.
Agent-based vulnerability scanning requires the installation of a software package (called an “agent”) on each device you want to test. Each agent collects security-relevant data from its host machine and sends it back to collection servers. In this way, device data from across the infrastructure is collected and consolidated to provide a holistic view for easier analysis.Organizations with many remote employees often prefer agent-based scanning; it allows them to collect data from devices outside the company network.
Agent-based scanning has several advantages:
- Ideal for distributed environments. Organizations with many remote employees—an on-the-rise trend—often prefer agent-based scanning as it allows them to collect data from devices outside the company network.
- Covers disconnected devices. Devices can be scanned even when they aren’t connected to the network, and agents will send data back to collection servers when an internet connection is reestablished. This allows scans to be paused
and restarted when a connection is interrupted, making it
well suited for traveling employees and others with intermittent Wi-Fi access. - Supports BYOD. With more employees using personal devices to connect to the corporate network, security risks are increasing. Agent-based scanning allows you to monitor these devices and enforce security policies.
- No credential requirements. Because the agents are installed directly on a device, there’s no need to log in to run a scan, as is required for some network-based scanning tools.
The main drawback: administrative overhead. Agents must be deployed to each existing device—and on new devices as they’re added to the environment—and agents may not exist for certain devices, like IoT hardware. Updates, if not automated, will also require extra work from IT teams.
In contrast, network-based vulnerability scanning involves centralized software that reaches out from a server to all network devices without requiring you to install and manage software on each one. This makes it easier to set up than agent-based scanning.
There are two types of network-based scanning: authenticated and unauthenticated. Authenticated vulnerability scanning enables you to log in to each device as a user, which allows you to see more of the system and find more vulnerabilities, than unauthenticated scanning. Unauthenticated vulnerability scanning relieves the burden of having to manage multiple login credentials, but its reduced visibility into various systems means it typically will only uncover basic configuration issues and errors.
[Read also: 10 ways Tanium makes configuration management better]
In either case, network-based vulnerability scanning offers several advantages over agent-based scanning:
- No compatibility requirements. Because there are no agents installed on network devices, there are no operating system requirements to detect and scan them. Network-based vulnerability scanning allows you to include IoT (Internet of Things) and network-based devices, such as switches and routers, in your scans.
- Deeper scanning. Network-based scanning can monitor all hosts and devices connected to the network, providing greater visibility and enabling you to scan assets that couldn’t be reached with agent-based scanning.
- Lightweight. With network-based scanning, you don’t have to install and manage software on your endpoints, easing manageability issues.
Ultimately, using only one type of scanning or the other will leave gaps in the amount and types of data you can collect from your devices. Only by combining both approaches will you achieve the comprehensive device vulnerability scanning you need to protect your organization from today’s range of threats.
What is a vulnerability and compliance assessment?
A vulnerability assessment is the process of identifying security weaknesses and risks in an organization’s devices and assets. It enables security teams, system owners, and other stakeholders to evaluate and prioritize vulnerabilities for remediation and secure their network environment.
Vulnerability assessments typically follow four stages:
- Identify vulnerabilities that could impact networks and systems.
- Evaluate those vulnerabilities to determine their degree
of severity. - Remediate all of the most critical vulnerabilities to
prevent exploitation. - Report on vulnerabilities to improve future security measures.
The average enterprise IT environment contains thousands of vulnerabilities. Vulnerability assessments provide essential information for security teams to identify the most critical risks and threats, enabling them to prioritize which weaknesses to address first. The assessment tools also recommend actions to mitigate and fix the identified vulnerabilities.
Vulnerability assessment scans are also necessary to ensure that organizations are meeting regulatory standards: Healthcare, financial, and government organizations face investigations and fines for noncompliance.
While regulatory requirements vary by industry, virtually all of them impact IT. Assessments can uncover vulnerabilities that may put the confidentiality, availability, and integrity of customer and patient data at risk. Further, assessment tools can be used to perform custom compliance checks for various regulatory requirements.
HIPAA and HITECH (the Health Information Technology for Economic and Clinical Health Act), for example, require healthcare organizations to audit login events, meet rules for complex passwords, terminate sessions within a predetermined time, and more for effective medical device vulnerability management. Vulnerability assessments can help determine and report if a healthcare organization’s IT environment reflects these policies.
How are device vulnerability reports used?
Device vulnerability reports are used to summarize the findings of a device vulnerability assessment. A typical report will include an overview of how well devices and applications performed in the vulnerability scan and the organization’s overall risk level based on the number and severity of vulnerabilities identified. The information in this summary will usually be represented through charts and graphs, and is targeted to C-level executives and other managers, offering a big-picture look at an enterprise’s device security risk and any issues that must be addressed.
Subsequent sections in the report will provide an overview of tools and activities used in the vulnerability assessment, a detailed accounting of the assessment’s results, and recommendations for mitigation or remediation.
How is device risk calculated?
Device risk is calculated using several factors. A vulnerability’s severity score weighs most heavily in the calculation, as it indicates the potential impact of an exploit. However, organizations must also consider the likelihood of a device to be exploited, the business assets at risk, the security measures already in place, and more.
A vulnerability on an internet-facing server would merit a higher risk score than that same vulnerability on a seldom-used test server, for example.
What is vulnerability remediation?
Vulnerability remediation is the process of fixing cybersecurity weaknesses in network devices, applications, and assets. Depending on the vulnerability, this may be done by patching or updating software, correcting or replacing code, or improving and enforcing security policies.
Effective vulnerability remediation is a critical part of securing modern IT environments. As IT infrastructures expand and become increasingly complex, vulnerabilities can easily proliferate. Corporate networks are under siege as threat actors target these weaknesses for bigger and bigger payloads. Vulnerability remediation is critical in this environment to reduce the risk of DoS attacks, data breaches, ransomware threats, and other costly security incidents.
Vulnerability remediation isn’t just a sound cybersecurity strategy, it’s also a common mandate of government regulations and industry standards. Both HIPAA and PCI DSS require covered organizations to maintain vulnerability monitoring and remediation processes.
Most enterprise infrastructures contain thousands of vulnerabilities, and there is no way to remediate them all. Fortunately, only a small percentage of vulnerabilities will pose a threat to most organizations. The challenge is determining which ones are a threat to yours.
[Read also: What is incident response? Latest strategies and trends]
Neither relying solely on metrics, such as CVSS scores—which rate vulnerabilities according to the potential damage an exploit would inflict—nor on gut feeling is an effective way to decide which vulnerabilities to remediate. Rather, a strategy that combines threat intelligence that can identify what vulnerabilities attackers are targeting, risk scores generated by vulnerability management tools, and the business context of your organization’s assets is the best way to focus threat hunting efforts. This will enable you to prioritize the vulnerabilities on the systems in your environment that are most likely to be exploited.
What does a vulnerability report look like?
A typical vulnerability looks like this:
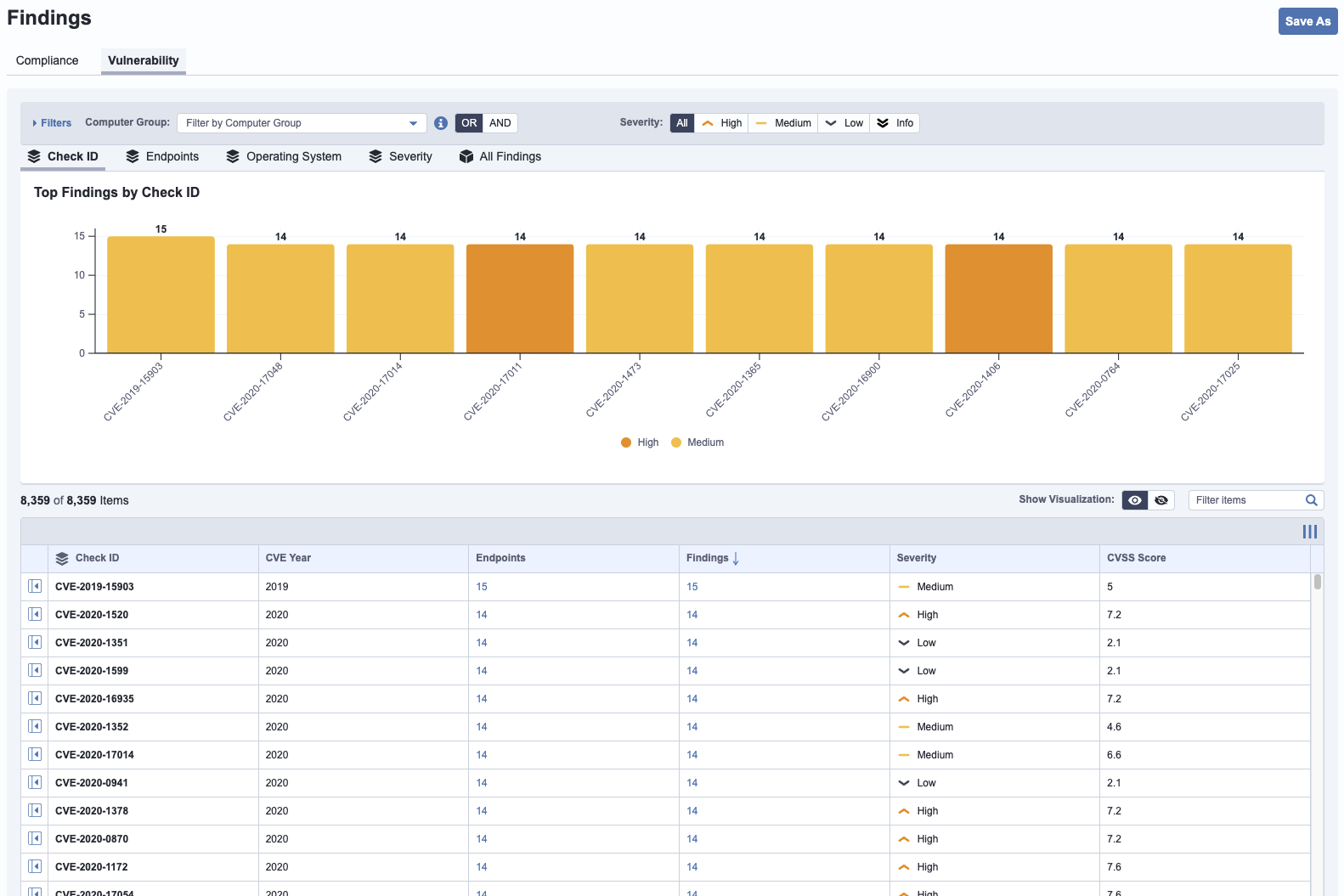
What are the challenges involved with device vulnerability management?
The main challenge of device vulnerability management is dealing with the breadth and heterogeneity of devices in modern IT environments. A single large enterprise can have hundreds of thousands of different devices inside and outside the corporate network that aren’t always online at the same time and which rarely have the same controls.
The diversity of devices on enterprise networks has also grown to include smartphones and tablets, as well as IoT devices like thermostats and sprinkler systems. This can greatly complicate vulnerability scanning and underscore the need for flexible device vulnerability management tools.
What should I look for in a device vulnerability management tool?
Almost any device vulnerability management tool will be able to identify security vulnerabilities in your environment. The important question is whether it can do so quickly and at scale.
[Read also: Cybersecurity in manufacturing—managing risk at scale]
Timing is critical. Organizations can’t afford to wait weeks to get a vulnerability assessment report in today’s fast-moving threat landscape. An effective device vulnerability management tool should be able to identify risks impacting your organization in minutes without having to scan after-hours or only during low network loads. It should also be able to cover the diversity of devices on your network, including legacy machines and IoT devices. An enterprise-ready tool should also be able to run a variety of vulnerability assessment reports to meet the information needs of both senior executives and operations staff.








